Why maintenance isn’t a strategy anymore
What breaks first isn’t always the code, it’s the silence.
Most mission-critical systems don’t fail overnight. They decay in silence, hidden behind vendor “support contracts,” quarterly patch cycles, and brittle legacy stacks no one wants to touch.
Then one day, a dashboard stalls. A patch collides with something undocumented. A regulatory audit flags a system that hasn’t evolved in a decade. You didn’t change anything, but suddenly, nothing works.
This is what happens when “maintenance” becomes your default strategy.
The problem isn’t the aging system itself. It’s that your vendor stayed passive while your risks accumulated. No roadmap. No migration plan. No warning. Just reactive support tickets and quiet technical debt piling up in the background.
87% of IT decision-makers say sticking to older IT systems
— Atera, 2024
Meanwhile, compliance windows tighten, support lifecycles expire, and your in-house team slowly loses the ability, or the will, to maintain the stack.
Take the Copperchase ATC system, which supports real-time operations at multiple airports across the UK and Europe. Originally built on .NET Framework, it became harder to support, harder to secure, and impossible to scale. Their previous vendor never flagged the risk. TYMIQ did, and took full ownership of the migration while keeping live operations running. No disruption. No finger-pointing. Just accountable delivery.
This is the real difference between a vendor who patches, and one who prepares.
In the sections ahead, we’ll break down when maintenance stops being viable, what vendor-led modernization actually looks like, and how to transition from risk containment to technical momentum, without grinding your operations to a halt.
Because doing nothing isn’t safe. It’s just expensive, slow, and hard to reverse.
Primer: What is software modernization?
Modernization isn’t one decision. It’s five.
Too often, “modernization” gets flattened into a buzzword, when in reality, it’s a decision tree. Rehost, replatform, refactor, rearchitect, or rebuild? The answer changes depending on what you’re running, how it's breaking, and what the business needs next.
If you’ve ever heard a vendor say “let’s just refactor it” without first mapping the stack, dependencies, or compliance surface, that’s not modernization. That’s a guess.
Here’s how real modernization decisions break down:
Let’s call it what it is: maintenance preserves debt. Modernization converts it.
A system running on .NET Framework today is already in countdown mode. .NET Core, .NET 6, and now .NET 8 offer performance, security, and long-term support your current stack simply can’t replicate, no matter how much maintenance you fund.
Modernization isn’t about chasing the latest tech. It’s about buying time back from entropy.
Case study: Modernizing ATC systems
When your system keeps planes moving across multiple airports, "just keep it running" doesn’t cut it. That was the challenge Copperchase faced.
Their Air Traffic Control Information Display System (ATC-IDS) built on .NET Framework, was operational but brittle. The original vendor had long exited. There was no in-house technical ownership. And with upcoming regulatory thresholds like CAP 670 ATC02.36, risk wasn’t hypothetical. It was already on the audit sheet.
The challenge
- Legacy stack. The .NET Framework base couldn’t reliably support the full range of airport environments.
- No internal ownership. With zero in-house expertise, even minor issues created major friction.
- Vendor silence. No roadmap. No risk calls. Just reactive fixes, until that stopped being enough.
“We couldn’t maintain our legacy system alone, and we weren’t getting forward-looking input from our previous provider.”
— Tony Myers, Director of Business Development, Copperchase Limited
The modernization approach
TYMIQ stepped in under a dual mandate: keep the live system fully functional and lead the modernization to a secure, future-ready architecture.
What they delivered:
- Parallel migration to .NET Core, maintaining full functionality throughout
- Modernized web-based UX to replace the old thick-client interface
- Compliance-secure deployment in line with UK’s CAP 670 ATC02.36 regulations
- Zero disruption to real-time operations at any airport site
Meaningful results
Instead of a tech upgrade, it was a full-stack operational shift that protected Copperchase’s core business while modernizing around it.
Why it worked
- TYMIQ took full ownership, not just code maintenance, but forward planning, compliance assurance, and rollout logistics
- No waiting for things to break; modernization began before the platform hit a wall
- Delivery-first mindset, with ongoing post-launch support, not just a handoff
“TYMIQ identified risks early, communicated clearly, and ensured everything transitioned without breaking ops.”
— Tony Myers, Copperchase, 2024
Mini-case: Failing forward in port operations
Not every legacy story ends in success. Some drag out until failure becomes visible and costly.
At a major seaport in the MENA region, a legacy logistics system ran the backbone of cargo tracking, customs communication, and SLA monitoring. It was functional. But slow. And slowly falling behind.
The vendor kept patching.
Until the system’s main dashboard, the one responsible for real-time cargo handling decisions, began taking 20+ seconds to load. Operators couldn’t meet SLAs. Reports lagged. And business users flagged delays as operational risk.
The port had no modernization roadmap. No observability stack. And no internal team to unwind the complexity of DevExpress and Web Forms.
The wake-up moment
- SLA breaches triggered penalties
- Internal users began bypassing the system
- Integration blockers stalled a customs digitization initiative
By the time TYMIQ was brought in, the system had lost trust, but not viability.
The recovery plan
Instead of rewriting everything from scratch, TYMIQ engineered a parallel modernization path:
- Refactored core features into a modern stack: .NET Core + React
- Migrated gradually, ensuring 24/7 operations never broke
- Preserved legacy business logic, reducing disruption for operations teams
The result is a new system called OGEN 2.0 with faster dashboards, cleaner architecture, and full integration with customs APIs, security layers, and reporting tools.
Lessons from the port
- Modernization after failure is totally possible, but harder
- SLA damage and user distrust take longer to repair than code
- Vendor silence is also a signal
If Copperchase was an example of proactive modernization, this case shows the opposite: a costlier, riskier, and less predictable path.
Both cases ended in success. Only one avoided a crisis.
5 red flags you’ve outgrown maintenance
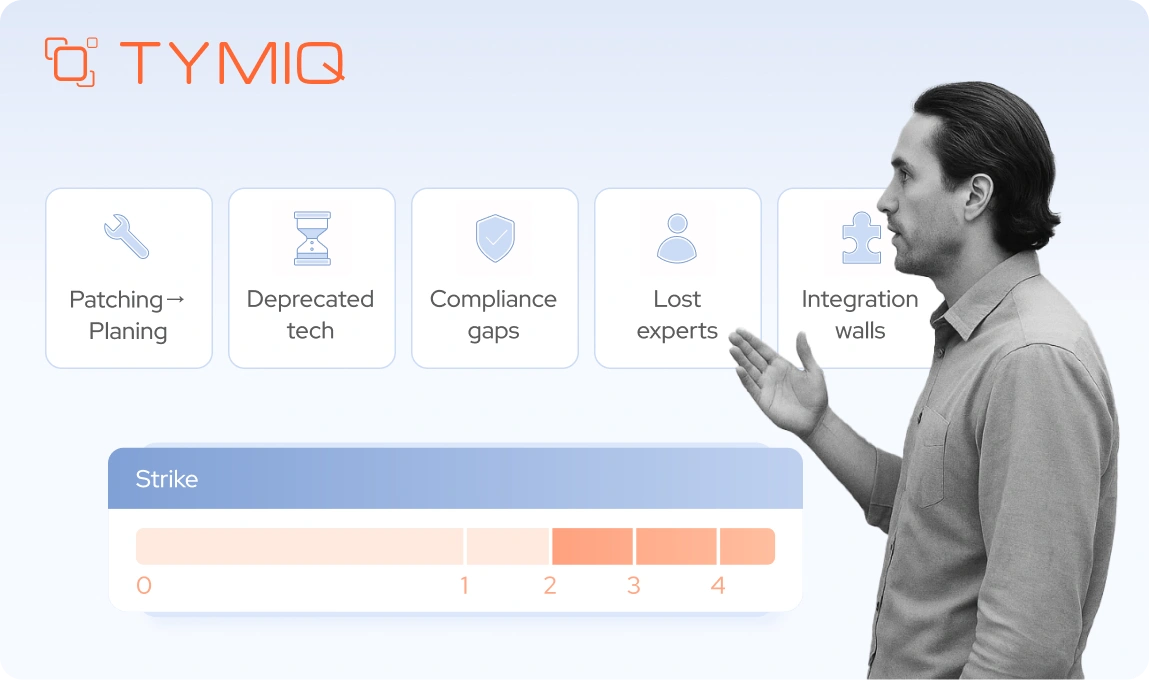
You don’t need a system outage to know it’s time. You just need to recognize the patterns.
Modernization doesn’t begin with a tech crash. It begins with small, repeatable signs that your system isn’t built for what’s next.
Here are the five most common flags that signal you’ve passed the point of sustainable maintenance:
1. You’re patching more than planning
Your dev queue is full of bug fixes, minor compatibility tweaks, and emergency workarounds. Roadmap conversations never happen because you’re stuck reacting, not building.
Diagnostic cue: If 3+ consecutive sprints are fix-focused, not feature-driven, you’re in reactive mode.
2. Your stack is stuck on deprecated tech
You’re still running on .NET Framework, Java 8, or old Web Forms. You’re increasingly locked out of modern libraries, tools, and cloud-native benefits.
Examples:
- .NET Framework loses major update support in Jan 2029
- Java 8 has been end-of-public-updates since 2020
- DevExpress dependencies are causing browser-level UI issues
3. You can’t meet new compliance mandates
GDPR. ISO 27001. CAP 670. If your system can’t generate the logs, control access, or support full audit trails, you’re exposed, legally and operationally.
Common pain: Manual logs, missing SBOMs, outdated encryption protocols.
4. You’ve lost your internal experts
When the original devs leave, what’s left is code without context. Knowledge gaps turn small changes into major risks, and vendor silence compounds it.
Risk signal: “We don’t touch that module anymore. We don’t know what it might break.”
5. You’re hitting integration walls
New tools like AI copilots, IoT sensors, and real-time analytics can’t connect to your system without months of retrofitting. API limits, auth gaps, and a monolithic structure block progress.
Impact: Business units start running shadow IT to bypass system constraints.
The 3-strike rule
If your system matches three or more of these flags, you’re past the point of "just maintaining." You need a vendor who can phase out your technical debt without halting operations.
The modern vendor mandate: Anticipate, advise, align
A modern system needs a modern vendor, not just one who shows up when things break, but one who helps you outpace that breakage entirely.
This is what separates tactical contractors from strategic partners. Maintenance vendors wait for tickets. Modernization vendors do three things consistently:
1. Anticipate
Flag risks before they turn into outages. A vendor should be scanning your tech surface like it’s their own, identifying performance bottlenecks, compliance deadlines, and stack deprecation before they impact uptime.
Observable behavior:
- Quarterly tech risk report
- Lifecycle visibility across stack versions and vendor dependencies
- Alerts tied to end-of-support, not end-of-function
2. Advise
Push modernization paths that aren’t vague or hand-wavy. They should show staged options, cost modeling, and a roll-forward/roll-back strategy.
Observable behavior:
- Modernization proposal tied to TCO impact
- Multiple migration paths with staffing and security implications
- Vendor aligns build decisions with current regulatory timelines
3. Align
Connect technical execution to business goals, not abstractly, but with traceable outcomes tied to OKRs, risk metrics, and operating models.
Observable behavior:
- Roadmap aligned to compliance checkpoints
- UX improvements mapped to adoption or error reduction
- Dev velocity tied to product delivery goals
Proactive vs. reactive vendor table
Modernization ROI: The CFO’s view
Modernization doesn’t just lower risk. It redefines cost structure.
From a CFO’s lens, the value of modernization is rarely about tech for tech’s sake. It’s about where the money goes, and how fast it stops leaking.
“Why change something that still works?”
Because it’s costing you more than it returns, and the failure curve is steeper than it looks.
Where the real ROI comes from
ROI snapshot from real cases
- Break-even: 14–18 months (parallel run model)
- Risk-adjusted IRR: 22%
- Audit costs: ↓ 40%
- Support tickets: ↓ 60%
- Delivery frequency: ↑ 2×
- Compliance flags: ↓ 100% → 0%
This is not theoretical. These are tracked outcomes from projects in aviation, logistics, and infrastructure systems, including the modernization of Copperchase ATC-IDS and a port operations system.
Use the right modeling tools
To make the case stick internally, tie the modernization approach to total cost of ownership (TCO) and de-risked execution. We recommend showing:
- Two model paths
→ Parallel run: Modernize alongside legacy, cut over when stable
→ Big bang: Replace core modules at once (higher risk, higher velocity) - 12 vs. 24-month cash flow map
→ Show when the burn peaks and when it normalizes - CapEx vs OpEx shift
→ Cloud-native + containerization often reshapes budget line items
The hidden value beyond cost reduction
Not everything that matters shows up in the budget. Modernization isn’t just cheaper, it’s safer, faster, and more trustworthy in ways finance teams can’t always quantify.
The truth is, many modernization initiatives succeed not because they saved money, but because they restored confidence.
Here’s where the value hides:
1. Improved compliance posture
Regulatory velocity is increasing. Legacy systems rarely keep up, and manual compliance doesn’t scale.
With modernization:
- Audit trail coverage goes from partial to automated
- SBOMs and software provenance are trackable
- Compliance timelines become part of deployment cycles
2. Faster time-to-change
Modernized stacks unlock speed. Not speed for its own sake, but for recovering from failure, responding to risk, and delivering upgrades without disruption.
3. User trust and operational clarity
The more critical the system, the more valuable trust becomes. Users lose confidence when dashboards break, updates are inconsistent, or support teams don’t respond with clarity.
Modernization brings:
- Predictable UX behavior across devices and browsers
- Smoother onboarding for new team members or operators
- Easier cross-team visibility into what’s deployed and why
Strategic takeaway
Cost savings are the floor. But compliance, velocity, and trust form the ceiling. That’s what enables scale, supports investor confidence, and prevents operations from grinding under silent tech debt.
The cost of waiting (+ timeline benchmarks)
If modernization feels expensive, try waiting.
What most leadership teams underestimate isn’t the effort of modernization, it’s the compound cost of inaction. And it rarely comes from one dramatic failure. It creeps in quietly:
- A missed audit window
- An integration that falls apart mid-rollout
- A lead developer who finally quits, and takes system knowledge with them
Each delay adds drag to your business. And the deeper your tech debt, the harder the exit.
Hidden costs hiding in plain sight
Note: These aren’t edge cases. They’re recurring themes across aviation, logistics, fintech, and healthcare.
Timeline callouts you can’t ignore
How to spot the stall
- You’re hearing “we’ll revisit this next quarter” every quarter
- Budget conversations frame modernization as “non-urgent”
- Your team avoids touching parts of the system or refuses to own them
Sector snapshots: Beyond aviation
The challenges of legacy maintenance aren’t limited to runways and control towers. Across industries, from healthcare to defense, the signs of stack fatigue are nearly identical.
The difference? Some sectors are modernizing at speed. Others are stacking risk by default.
Here’s how different sectors are approaching vendor-led modernization.
Healthcare
| Mandate | HIPAA, FHIR 5.0, patient data sovereignty |
| Blocker | Hardcoded billing logic, EMR silos |
| Vendor Fix | API-first modularization, FHIR-compliant microservices |
Defense and security
| Mandate | ISO/IEC 27001:2022, SBOM tracking, Zero Trust |
| Blocker | Security patch gaps in unscalable monoliths |
| Vendor Fix | Secure replatforming, automated audit trails, SBOM infrastructure |
Logistics and port operations
| Mandate | 24/7 SLA delivery, customs digitization, real-time visibility |
| Blocker | Legacy browser-locked UI, slow dashboards, siloed data |
| Vendor Fix | Cloud-native UI, real-time sync, hot-patching for zero-downtime ops |
What these sectors have in common
- High audit pressure
- High system uptime requirements
- Legacy stack exposure hidden in “functional” systems
- Heavy vendor reliance, often without modernization accountability
Instead of copy-pasting aviation playbooks, you should recognize shared risk patterns and demand the same level of vendor foresight in every regulated industry.
Your roadmap: Modernizing in regulated environments

Modernization in theory is easy. Modernization with audits, regulators, and zero-downtime mandates? That’s where most vendors flinch.
If you're in healthcare, aviation, logistics, or defense, the playbook can't just be "move fast." It needs to be structured, staged, and reversible, all while keeping live operations stable.
Here’s how that actually works.
3-phase vendor-led modernization model
Use this when building consensus with internal teams, auditors, or procurement. It shows that speed and control aren’t mutually exclusive.
Goal: Build situational clarity before touching code.
- Inventory systems (incl. dependencies and shadow IT)
- Run static analysis on legacy components
- Map compliance obligations: ISO 27001, HIPAA, CAP 670, etc.
- Document third-party integrations (and their constraints)
- Flag security vulnerabilities and change blockers
Output: Risk register + modernization readiness snapshot
Goal: Prove it can work without risking everything.
- Choose low-risk, high-leverage modules for parallel migration
- Use blue/green deployment or canary releases
- Run pilots with rollback plans built in (not bolted on)
- Involve compliance stakeholders early, not post-facto
- Validate test coverage, CI/CD readiness, and rollback time
Output: Stable modernized module, performance data, rollback validation
Goal: Scale change while maintaining visibility and control.
- Establish CI/CD pipelines with audit trail support
- Enable observability: monitoring, alerting, traceability
- Gradually replace legacy endpoints and interfaces
- Introduce change windows aligned with regulatory cycles
- Train internal teams on new support and escalation workflows
Output: Production-grade modernization, phased cutover, continuous compliance
Included toolkit (for download or workshop use)
- Risk register template: system-level risks, linked to business and compliance impact
- Vendor readiness checklist: what to demand before signing a modernization contract
- Audit sync calendar: how to map modernization phases to ISO/GDPR/CAP audit timelines
Strategic reminder
Don’t hurry and break things. Instead, you need to move smart and prove readiness.
That’s what modern vendors build for, not just deployment velocity, but predictable outcomes under constraint.
Future-proofing with AI, cloud-native and zero trust
Modernization isn’t just an upgrade. It’s your admission ticket to everything next.
Whether it’s AI deployment, real-time analytics, or Zero Trust compliance, none of it works on brittle stacks. To unlock future capabilities, the foundation must be modular, observable, and secure by default.
Here’s how the best vendors build for future-readiness, not just recovery.
AI-ready infrastructure
AI isn't plug-and-play. It needs clean data, modular components, and system observability or it turns into shelfware.
Enablers:
- Kubernetes or containerized deployment
- Modern API design (REST/gRPC)
- Feature flagging for ML experimentation
- Message bus or event stream infrastructure (e.g., Kafka, RabbitMQ)
Cloud-native resilience
Cloud-native isn’t about where you host. It’s how you build. It enables resilience, portability, and elastic scale, all crucial for AI/ML workloads and global teams.
- Self-healing containers
- Immutable infrastructure
- API-first services with version control
- CI/CD pipelines that allow frequent, low-risk deployments
Modern foundation stack: Kubernetes + .NET 8 + OpenTelemetry
Zero trust architecture
Modernization makes Zero Trust possible. Legacy systems rely on implicit trust, static credentials, and brittle perimeter defense. That no longer holds.
Modern vendors build systems that assume every user, service, and device could be compromised and validate everything accordingly.
Core capabilities:
- Role-based and attribute-based access control (RBAC/ABAC)
- Tokenized authentication (e.g., OAuth 2.0, JWT)
- Service-to-service identity verification
- End-to-end encryption and audit logging
In defense, finance, and infrastructure, this isn't a nice-to-have. It’s a precondition for operating.
Software provenance and SBOMs
Future systems won’t just need to work. They’ll need to prove what they’re made of, for security, licensing, and liability.
Modernization enables:
- Software Bill of Materials (SBOMs)
- Dependency scanning (OWASP, Snyk, CycloneDX)
- Signed build artifacts for supply chain integrity
TL;DR: What you're building toward
Lessons from failed modernization attempts (playbook)
Not all modernization projects land safely. Some crash early. Some never leave the hangar. And most of the time, the root cause isn’t the tech, it’s the approach.
Here are the most common failure patterns, and the playbook to prevent them.
Playbook: If this… then that
Don’t just evaluate success — study failure patterns
These aren’t isolated incidents. They’re repeats across sectors:
- Ports migrating to cloud but failing to test third-party data syncs
- Healthcare systems rewriting frontends with no audit hooks
- Aviation tools rebuilt, but without user input and failing adoption
- Government agencies with vendors who never flagged that their stack was EOL
Vendor checklist (non-negotiables)
If your vendor isn’t doing these, you're headed for trouble:
Strategic shift
The goal of modernization isn’t perfection. It’s control under change, with visibility, rollback paths, and accountability baked in.
Conclusion: Is your vendor just patching or preparing?
By now, you’ve seen the patterns.
- Legacy systems aren’t failing suddenly, they’re eroding quietly.
- Maintenance isn’t strategic, it’s survival.
- And vendors who don’t raise flags early aren’t “playing it safe.” They’re passing the risk to you.
The question is no longer whether modernization matters. It’s whether your vendor is making it possible.
Copperchase modernized without disruption.
A seaport fixed 20-second dashboard latency.
Audit-readiness jumped from 70% to 100%.
All of it was driven not just by code, but by vendors who flagged risks early, staged migrations carefully, and stayed accountable end-to-end.
Ask yourself or your vendor:
- Have we mapped our modernization path, or are we stuck in patch cycles?
- Are we spending 70% of our budget just to stay upright?
- Can we meet compliance targets next year, or are we rolling the dice?
- Has our vendor helped us model the cost of waiting?
- Are we being advised, or just being billed?
If the answer isn’t clear, that is your answer.











.svg)

