Many enterprise applications still prompt users to log in. It happens even after they have already authenticated through their Windows session. This disconnect creates friction where browser-based Single Sign-On does not apply.
The result is slower onboarding, conditional access issues, and an increase in login-related support tickets.
This article explains why desktop SSO often fails in enterprise software, and how a brokered authentication model using Keycloak and Microsoft Entra ID can help you resolve those gaps. It covers when this setup is necessary, how to implement it, and what outcomes to expect based on real deployments.
Why desktop SSO fails in modern enterprise SaaS
Most apps assume browser context
Modern SaaS products are typically built for the browser. They rely on web-based authentication flows using tools like OAuth or OIDC. This reliance assumes users interact through Chrome, Edge, or Safari. But your desktop applications don’t run in a browser context. To align with modern identity flows, they need to access the Windows Account Manager (WAM) and use Microsoft’s Authentication Library (MSAL).
Without WAM or MSAL integration, your desktop app won’t inherit the user’s signed-in state from the device. The result is redundant login prompts, even when the user is already authenticated at the operating system level.
Conditional Access is enforced upstream, not inside the app
You might assume Conditional Access (CA) rules will apply automatically. But they only trigger through supported identity flows. If your app isn’t properly connected to Entra ID, CA rules like location or device checks are either bypassed or inconsistently enforced. And if you try to enforce CA logic directly within the app, you fragment your audit trails and increase compliance risks.
Legacy login logic blocks modern IDP integration
Older desktop apps often rely on custom login workflows that don’t support token-based identity. You may still be asking for usernames and passwords directly or depending on cookie-based sessions. These outdated methods don’t align with Entra ID, Keycloak, or any standards-based identity provider. Attempts to patch these flows often fall short of delivering real SSO, and can undermine your security posture.
Real-world example
A security-focused SaaS client faced constant login friction. Their desktop app prompted users for credentials at every launch. Even though users were already authenticated in Windows. The support team logged complaints daily. Users lost trust, assuming the app was insecure or broken. Internally, the app failed to pass Conditional Access audits because it couldn’t confirm the session context.
Why this matters
Login friction erodes user trust. When enterprise users sign into Windows but still face manual app logins, it feels broken, especially in high-stakes tools.
Beyond UX, there’s risk. If your app doesn’t inherit the user’s Primary Refresh Token (PRT), it sits outside Entra ID’s Conditional Access. That means no real enforcement of MFA, device compliance, or session lifetime, even if the policy says otherwise.
This setup fixes that. It keeps identity enforcement where it belongs (in Entra), while giving your app seamless login and a traceable security posture.
Keycloak + Entra ID brokered identity for token consistency (but not seamless Windows login)
While Keycloak enables centralized token brokering and tenant routing, it does not support Seamless SSO (SSSO) for desktop apps when placed in front of Entra ID.
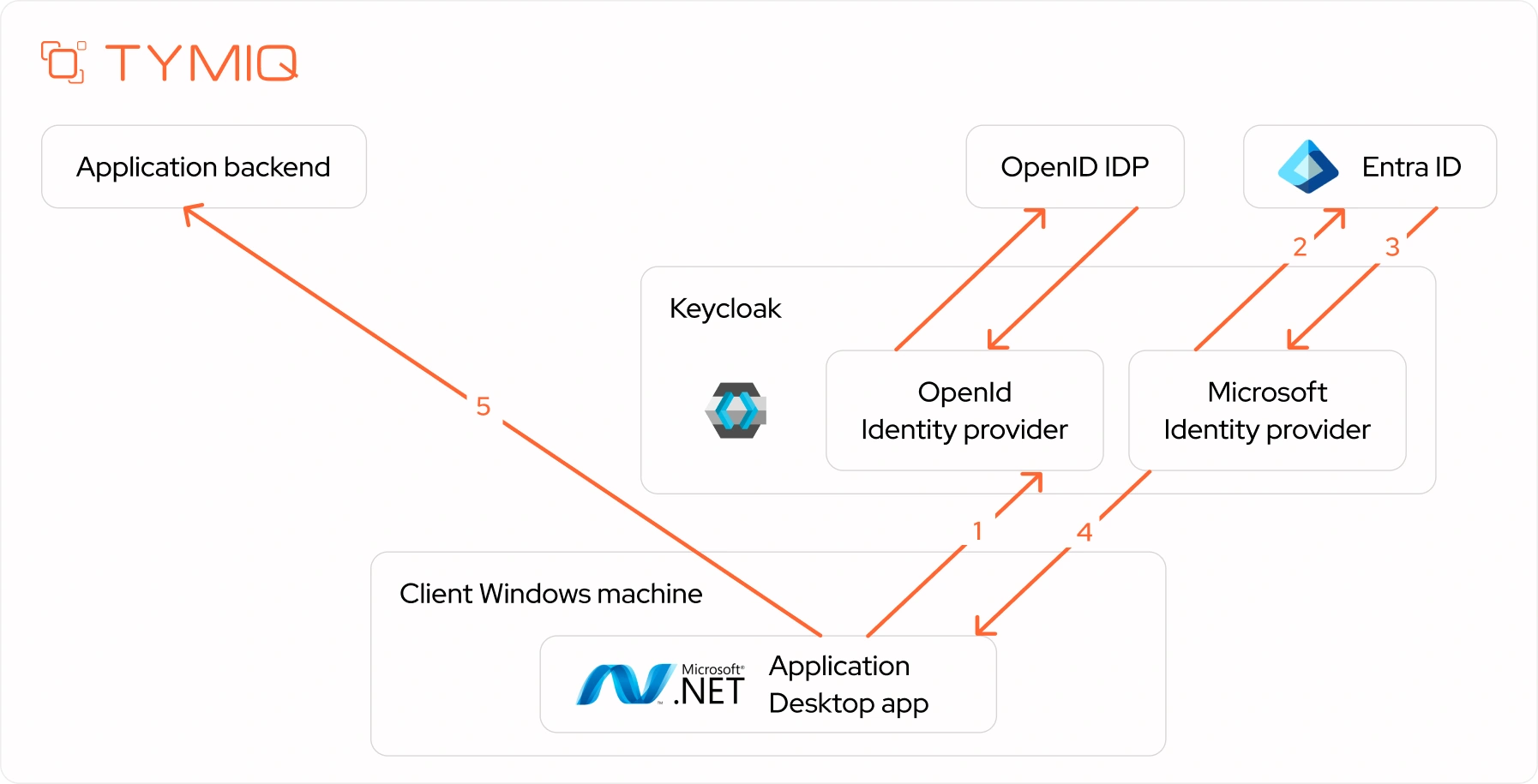
For true passwordless login from Windows, your desktop client must authenticate directly with Entra ID using MSAL and WAM. The brokered model is ideal for backend standardization rather than for preserving native desktop authentication flows.
Most identity issues in desktop apps stem from assuming the browser will handle everything. But once you shift outside of browser context, you need a smarter approach, one that bridges device login and IDP logic without rewriting every authentication flow.
That’s where the Keycloak + Entra ID pairing comes in. Used together, they create a brokered identity layer. This layer connects native Windows authentication with your SaaS app’s authorization logic.
Keycloak isn’t just a login provider. It’s the broker
Think of Keycloak not as an identity source, but as a routing engine. It detects which tenant a user belongs to, and translates token formats. Then, it hands off authentication to the appropriate IDP (in this case, Entra ID) and then issues a normalized, app-ready token back to your system.
This means you don’t have to rework your app to speak Entra directly. Instead, your app talks to Keycloak once, and Keycloak speaks to Entra (or any other IDP) as needed.
Why Entra ID alone isn’t enough for multi-tenant SaaS
Directly integrating each enterprise’s Entra ID into your app works until you need to support more than one. Then you’re faced with:
- Token claim mismatches between tenants
- Custom mapping logic for every new enterprise client
- Growing audit complexity
- Risk of inconsistent CA enforcement
While Entra ID lacks dynamic tenant routing, it is essential for desktop-level Seamless SSO. Keycloak complements this by centralizing token handling but cannot fully replace Entra for device-bound flows.
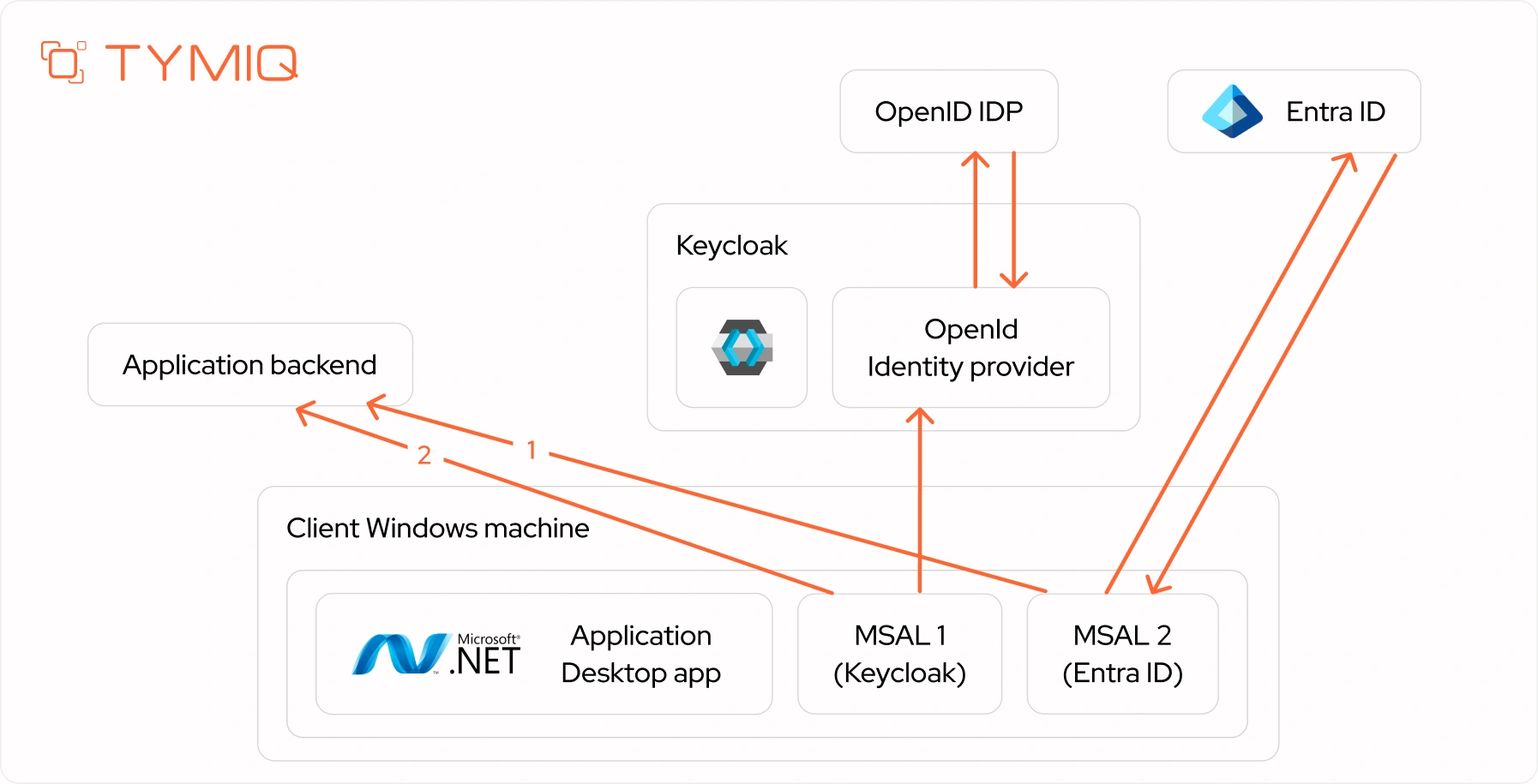
How brokered desktop SSO works - with Keycloak in the loop
- User signs into Windows, triggering the Windows Account Manager (WAM) to issue a Primary Refresh Token (PRT), securely tied to the device.
- A .NET desktop app uses MSAL to authenticate directly with Entra ID. MSAL reuses the PRT to silently acquire an Entra-issued token.
- The app forwards the Entra token to Keycloak. This step triggers a backend exchange where Keycloak validates the token
- Keycloak issues its own token. This token contains consistent claims (e.g., user_id, tenant, roles).
- The app uses the Keycloak-issued token to call the backend. The backend trusts only Keycloak tokens.
Important disclaimer
Seamless single sign-on via the primary refresh token and Windows Authentication Manager only works when MSAL talks directly to Entra ID. If Entra ID is fully hidden behind Keycloak, the primary refresh token cannot be reused and login becomes interactive. For real seamless single sign-on, a hybrid flow is required where desktop applications authenticate directly with Entra ID, while Keycloak handles backend token brokering.
Glossary — key terms
- WAM (Windows Account Manager): Component that issues PRTs after a successful Windows login.
- MSAL (Microsoft Authentication Library): SDK used to acquire tokens from Entra ID.
- PRT (Primary Refresh Token): Credential issued to domain-joined devices for seamless SSO.
- OIDC (OpenID Connect) vs. SAML: Two authentication protocols; OIDC is preferred for modern apps.
What you gain
- Faster onboarding: 2–4 week setup with pre-built plugins and token mappers
- Seamless Conditional Access: Entra enforces policies at the IDP level
- Token consistency: Your app sees the same structure, no matter the tenant’s IDP
- Seamless Windows login (SSSO): Only available when MSAL authenticates directly with Entra; not via Keycloak.
This approach is already deployed across multiple enterprise SaaS environments. It replaces brittle integrations with a scalable, compliant identity layer.
What’s not working in the industry (and why TYMIQ built differently)
.webp)
Enterprise SaaS providers often try to bolt identity into native apps the same way they do for browser flows. That usually works, until it doesn’t. When your enterprise clients demand real Conditional Access enforcement, seamless login from domain-joined Windows machines, and centralized auditing, those shortcuts fall apart.
Here’s where most teams run into trouble, and how TYMIQ’s brokered architecture avoids it.
Why TYMIQ takes a different approach
Layering workarounds on top of incomplete integrations isn't a good idea. Instead, TYMIQ built a brokered architecture that:
- Centralizes all tenant and IDP logic in Keycloak, not your app
- Uses Entra ID for policy enforcement, without requiring per-tenant rewrites
- Normalizes tokens once, upstream, giving your app a consistent trust contract
This approach minimizes what your engineering team has to manage, without losing visibility or control.
When you actually need this setup (and when you don’t)
Not every SaaS product needs desktop SSO with brokered architecture. But if your clients are enterprise buyers, the chances are growing fast. Use this quick diagnostic to decide if the Keycloak + Entra model fits your stack and user expectations.
Diagnostic checklist
Ask yourself:
- Do you support Windows desktop clients that run outside the browser?
- Do enterprise buyers require Conditional Access policies as part of procurement?
- Are support tickets piling up from login failures, reauthorization prompts, or session issues?
- Do you plan to support more than one IDP (Entra ID, Okta, Ping, etc.)?
- Do clients require audit-grade access logs tied to organizational policies?
If you answered “yes” to three or more, your current identity setup is likely a blocker, not a differentiator.
What to do next
The more “yes” responses you tick off, the more value you gain from introducing Keycloak as a centralized broker. This architecture is especially suited to:
- Security-focused platforms
- Regulated industries (finance, health, legal)
- Multi-tenant enterprise tools
- Native desktop experiences with shared identity needs
If none of those apply yet, you may be fine with browser-only SSO. But reconsider your identity architecture before it becomes a barrier to growth.
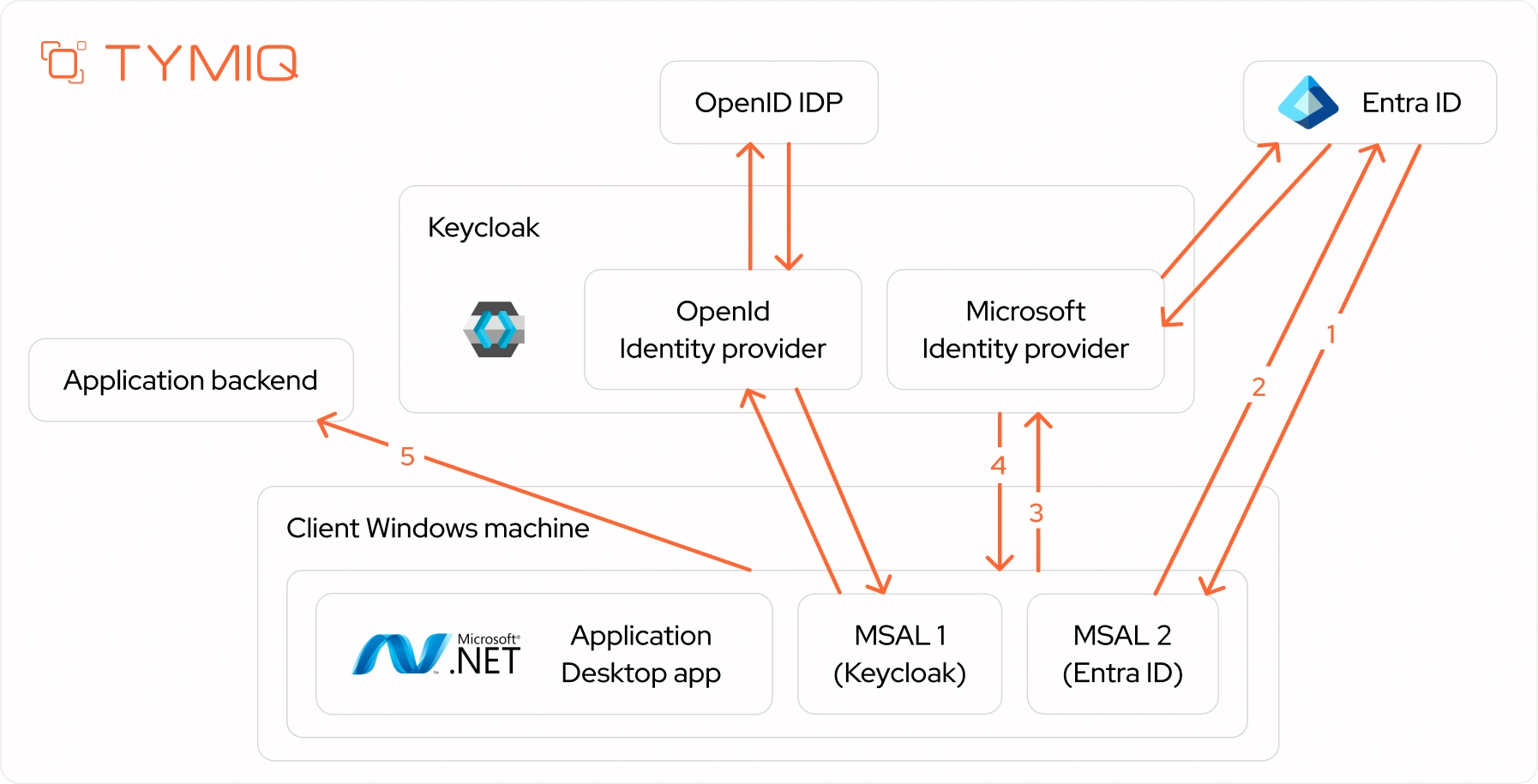
Hybrid model: Brokered backend + native Entra flow for SSO
The architecture below reflects a hybrid brokered model, where MSAL on the desktop uses direct Entra ID integration to preserve seamless SSO, while Keycloak still centralizes backend trust and token validation.
Flow
- MSAL2 requests a token directly from Entra ID (supports PRT, SSSO, and conditional access).
- Entra returns a native access token and an ID token.
- MSAL1 sends the Entra token to Keycloak for normalization.
- Keycloak returns a signed, app-specific token.
- The app calls the backend using only the Keycloak-issued token.
Why this works
- Seamless UX. Users get passwordless login via Entra ID using PRT and WAM.
- Centralized trust. The backend only verifies Keycloak-issued tokens.
- Strong policy enforcement. Conditional access is applied before Entra issues a token.
- Minimal disruption. Desktop apps stay MSAL-compatible and require no deep protocol rewrites.
Why can you not fully hide Entra behind Keycloak
If MSAL talks only to Keycloak, and Keycloak then calls Entra, you lose:
- PRT-based login.
- TPM-bound token reuse.
- Seamless desktop SSO.
That’s why full Keycloak brokering works for browser or backend use cases but not for desktop-native flows that depend on WAM/MSAL/PRT.
Designing the ideal brokered SSO: making Keycloak and Entra ID work together
Rather than viewing Entra ID and Keycloak as competing layers, the most resilient architecture treats them as complementary parts of a secure identity stack. Seamless desktop login and centralized token brokering don’t need to be mutually exclusive if you split responsibilities wisely.
The division of responsibility
Let Entra ID handle who the user is, under what conditions they can log in, and what device they are using. Let Keycloak determine how your backend understands and trusts the resulting identity.
Core principle: authenticate natively, normalize centrally
When you separate authentication from authorization, you unlock flexibility without sacrificing security. This approach leads to:
- Seamless user experience via native login
- Strong Conditional Access enforcement
- Unified backend logic for all tenants and identity providers
- Easier onboarding of new clients without rewriting application code
Integration patterns that work
Token exchange layer
Use Keycloak’s token exchange feature to convert Entra-issued tokens into signed, normalized OpenID Connect tokens. This ensures:
- Backend sees only tokens it understands.
- You avoid tenant-specific logic downstream.
- You can enrich tokens with additional claims (for example, internal roles, org metadata).
Custom mappers for claim normalization
Each enterprise Entra tenant may issue slightly different claim formats. Use Keycloak custom mappers to translate these into a consistent schema across:
- user_id.
- roles.
- tenant.
- scopes.
Hybrid MSAL clients
Set up two MSAL clients in the desktop app.
This aligns with the 3.2 diagram. Silent login comes from Entra; backend trust comes from Keycloak.
Scoped token TTLs + refresh logic
Let Keycloak issue tokens with shorter lifespans than Entra to allow for fast revocation or policy updates without affecting upstream authentication sessions.
Fallback path for MSAL disruption
If MSAL fails or the primary refresh token is unavailable (for example, on non-domain-joined machines), gracefully fallback to browser-based login via Keycloak. This ensures access continuity without forcing a degraded experience on all users.
Where this pays off
- Security-first industries (finance, health, critical infrastructure) that require both policy enforcement and audit traceability.
- Multi-tenant SaaS platforms with clients using Entra ID, Okta, Ping, or other OpenID providers.
- Desktop-heavy environments that cannot rely on browser sessions to carry identity.
- DevOps-focused organizations that want to simplify token validation and cut custom logic.
Security enhancements
To harden your implementation:
- Device binding. Bind tokens to TPM-verified hardware
- Proof of possession. Require PoP for sensitive actions
- Token cache encryption. Use OS-native storage (e.g., DPAPI or Keychain)
- Conditional Access. Enforce risk-based, step-up authentication when needed
Deployment patterns
- Shared realm with tenant mapping. Ideal for most SaaS platforms, centralized config and efficient routing.
- Dedicated realm per tenant. Best for high-compliance or high-risk environments needing strict isolation.
- Hybrid strategy. Mix both approaches based on customer tier or regulatory context.
Observability and monitoring
Track performance and compliance using structured metrics:
- Token acquisition latency
- Authentication success rate
- Cache hit ratio
- Per-tenant failure rates
Feed this data into your SIEM or observability platform for diagnostics and audits.
Direct Entra vs. Keycloak-brokered: When to use which
Choosing between direct Entra ID integration and a Keycloak-brokered approach depends on your architecture, scale, and tenant complexity. Use the comparison below to guide your decision:
The Keycloak-brokered model reduces complexity, improves maintainability, and gives you centralized control. But only if your application serves more than one enterprise customer. Or if you need to standardize identity across environments.
For single-tenant, internal, or tightly scoped desktop apps, direct Entra ID integration may be simpler. But once you grow into multi-tenant territory, the broker model becomes increasingly strategic.
Pitfalls to avoid
Some teams get SSO working, but not reliably, securely, or at scale. These common missteps quietly erode trust, auditability, and long-term maintainability:
- Skipping WAM integration → Seamless desktop SSO breaks without it
- Letting every client implement their own flow → Inconsistent behavior and support chaos
- Treating Conditional Access as an app-side feature → Gaps in enforcement and audit coverage
- Ignoring claim normalization → Tokens break backend logic across tenants
- Assuming SSO is just a login screen → You miss critical compliance controls, logging, and context
Avoiding these mistakes improves UX and protects your roadmap, audit trail, and credibility.
Best practices to get it right
For stable, scalable, and secure desktop SSO with Entra ID and Keycloak, these principles matter most:
- Use Keycloak as the sole backend trust authority. Centralize all token validation, claim mapping, and tenant routing in one place. This way you can reduce complexity and avoid app-level logic duplication..
- Cache sessions via MSAL per device. Leverage MSAL’s secure token cache to support silent authentication and improve UX.
- Rely on Entra Conditional Access, not app-side logic. Delegate all policy enforcement to Entra. Avoid implementing custom device, location, or MFA checks within your app.
- Normalize all claims in Keycloak: Ensure consistent token structures across tenants and IDPs. It helps to prevent backend errors and reduce integration effort downstream.
- Design a fallback plan for WAM disruption. Support browser-based fallback flows when WAM is unavailable. Especially during early device registration or on non-Windows platforms.
- Use a hybrid approach when needed: For Seamless SSO, let MSAL authenticate directly with Entra ID. Use Keycloak for token brokering on the backend. This preserves native login UX without sacrificing multi-tenant control.
Security and compliance implications (SOC 2, ISO 27001)
A brokered Keycloak + Entra ID setup isn’t just technically robust. It supports enterprise-grade compliance out of the box. Here’s how this architecture maps to key security and privacy controls required by SOC 2 and ISO 27001:
This setup gives you confidence in login UX. Moreover, you get ability to meet the audit, privacy, and control requirements of security-focused enterprise buyers.
Objection handling from CTOs and CISOs
“Will this break our Conditional Access rules?”
No. All policies stay in Entra. Brokered SSO simply forwards identity, not control.
“What if WAM fails on the device?”
The app falls back to browser-based login. The user still gets in, and nothing breaks.
“Can this meet our audit standards?”
Yes. Keycloak logs every authentication step: who logged in, how, and with what device.
“Will we lose visibility across tenants?”
No. Keycloak normalizes claims across IDPs, so you get one consistent view.
“Do we need to refactor our login flow?”
Not for most apps. MSAL and OIDC handle the handshake, but your session logic stays intact.
Real case study - TYMIQ implementation (anonymized enterprise security app)
.webp)
This case outlines how TYMIQ implemented brokered desktop SSO for a Windows-based enterprise security solution used by 40+ corporations across finance and government sectors. Due to NDA restrictions, we’ll refer to the client’s product as App XXX.
The business challenge
Enterprise users were already logging into their Windows machines each morning with Entra ID credentials. But every time they launched App XXX, they had to log in again manually, sometimes multiple times per day.
Even though Conditional Access was enabled at the tenant level, it wasn’t enforced inside the app. Login tickets became the #1 support complaint. The security team couldn’t verify Conditional Access compliance or ensure audit traceability. Onboarding new users took over three weeks. So long-term term was due to confusion around login behavior and provisioning delays.
Before TYMIQ
- Passwords had to be entered manually on every launch
- Conditional Access policies didn’t extend into the app
- Onboarding took 3+ weeks
- Login-related tickets dominated support queues
The TYMIQ solution
TYMIQ deployed a Keycloak + Entra ID brokered setup, optimized for multi-tenant SaaS delivery and tightly integrated with Windows-native authentication. Key components included:
- Configuring Keycloak as the single authentication broker for all tenants
- Using MSAL + WAM to enable PRT-based silent login
- Ensuring Entra ID remained the enforcement point for security policies
- Normalizing token claims through Keycloak for secure backend compatibility
This hybrid model allowed App XXX to support multiple identity providers while maintaining centralized control of all issued tokens.
How it works (flow summary)
- Your app starts an OpenID request and redirects to Keycloak
- Keycloak silently routes the request to Entra ID
- If a valid session exists, Entra returns a token immediately; otherwise, the user is prompted
- Keycloak signs and returns a normalized token to your app
- Your app uses the token to access backend services securely and consistently
After TYMIQ
- SSO worked automatically from the Windows login
- Login tickets dropped by 70%
- Onboarding time dropped to 10 days
- CA enforcement became fully audit-traceable
- Token issuance was centralized for consistent backend validation
This case highlights when brokered desktop SSO isn’t just helpful but essential. If your app supports Windows clients, handles sensitive data, or serves B2B users expecting frictionless access and enterprise-grade security, this architecture is no longer optional.
In most cases, the hardest part is recognizing that you need this architecture at all. TYMIQ helps you connect the dots and deliver with speed, security, and scale.
See it in your stack
If your app supports Windows clients, serves enterprise users, or juggles multiple identity providers, you’re likely already facing the friction this architecture solves. You don’t need to redesign your stack, just broker it smarter.
Here’s how to take the next step:
- Download the “SSO Design Guide for SaaS CTOs”
A practical explainer on when brokered SSO is needed, how it works, and what to watch for in rollout. - Book a 15-minute architecture consult
Talk directly with a TYMIQ engineer. No pitch, just answers tailored to your stack. - Explore the Keycloak and Entra integration paths
We’ve prepared a GitHub example and annotated Keycloak doc set for your technical team. - Try an architecture sketch session
Let us walk your use case through an actual Keycloak-brokered flow. One whiteboard, real scenarios, zero fluff.
You’re closer than you think to seamless, compliant, and scalable desktop SSO. Let’s make it real.






.svg)

.webp)


.svg)

